|
|
|
|||||||||
|
|
||||||||||
|
||||||||
 |
 |
Rendering Piracy Harmless Shades of Gray
Rendering Piracy Harmless: A White Paper
Dr. Andrew Burt
Computer Science Dept., University of Denver
Science Fiction and Fantasy Writers of America, Inc.
The purpose of the Shades of Gray anti-piracy technique is to make pirated copies of (electronic or other) works -- books, music, films, software, art, etc. -- so hard to trust that ordinary people won't bother with them, and will purchase legitimate copies as they would if pirate copies weren't available. In other words, the purpose is to drive the financial impact of piracy down so close to zero as to not matter. Additionally, the purpose is to use this method to use pirate distribution channels for promotional purposes, as inexpensive advertising, to increase sales.
Shades of Gray is a consumer-friendly approach, one that eliminates the need for intrusive encryption / DRM (Digital Rights Management) schemes, over-reaching legislation, ineffective DMCA-based lawsuits, etc.
Table of Contents:
- Background
- Shades of Gray
- Related Work
- Manner of altering originals to produce "gray" copies
- Defeating work-arounds
- Impact
Background Electronic Piracy and counterfeiting cost industries billions of dollars per year -- $5 billion/year for music; $3 billion/year for film, which will rise as broadband becomes pervasive; and $15 billion/year for software. (There is as yet no significant impact on book publishing, but this is likely to change dramatically with the advent of digital paper, such as Philips is mass producing in 2005, or any other technology that gains pervasive consumer adoption for reading. The impact could then rival that on the music industry.)
Legislative, legal, educational, and technological approaches have not solved the problem, and generally have created consumer resentment. Shades of Gray aims to solve the piracy problem with no impact at all on non-pirating users and with minimal antogonism toward pirating users, with the goal of turning them into paying customers by converting piracy into a form of marketing.
The approach of Shades of Gray is as follows: With the copyright owner's permission, many different versions of the legitimate work will be released into the pirate (or counterfeit) channels, with the correctness of the various versions spanning the spectrum from almost completely correct to completely incorrect.
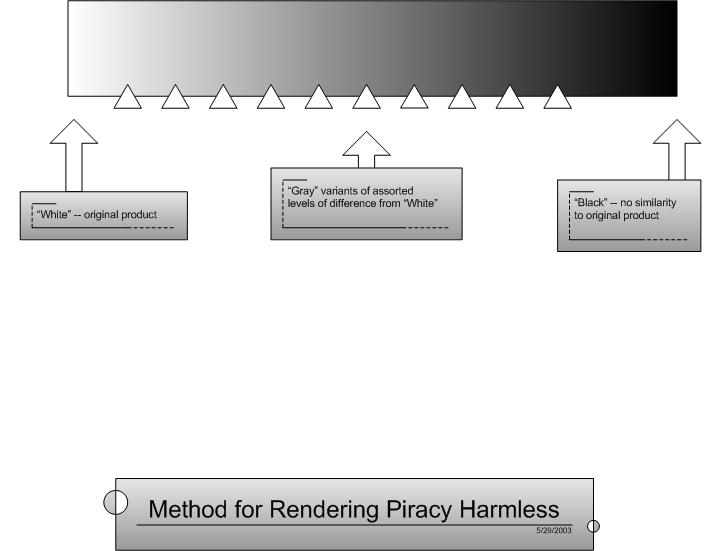
That is: If unmodified original files are considered the "white" version of that item, and files that are completely different are considered "black," then this is metaphorically like creating numerous shades of gray. Some gray copies may be nearly identical, some may appear to have no resemblance to the original, with many other points along that spectrum. With such a spectrum of carefully crafted incorrect/fake copies of the true un-pirated work it becomes extremely difficult to trust that one has found a "real" pirated copy.
The altered, "gray" copies will have all manner of changes made to them to make them different, and in may cases annoying to pirate users, as described below.
Thus the idea is to circulate, at the copyright owner's request, many, many variants of a work, ranging from pure noise to almost the exact real thing, and a plethora of shades of gray in between (e.g. 95% of real, 90%, 85%, 80%...10%, 5%, 0), making it extremely diffiecult for a downloader to tell how real a pirate work is.
These gray copies (but not the original) will then be released in all the manners that pirate copies are currently available, such as via peer-to-peer networks, on web sites, etc. This technique works similarly for conterfeit copies.
Then, pirate downloaders will have significant doubt about how real the file is they're stealing: It might be almost real (but are the words different in this song from what I remember from the radio?, or the music is different?, or for a movie some scenes are missing?, like the "Jar-Jar free" fake of Star Wars, where someone edited out the Jar-Jar character) -- but there's -something- wrong with it, they (or their friends) eventually discover: After investing significant time in it, they become aware it was a fake, and they wasted all their time. After a few hits of that most downloaders will sour on the usefulness of piracy.
It should be widely publicized this is being done. Thus they will not only find altered copies that are in varying degrees of difficulty to tell that they're altered, they'll also know in advance that copies exist in all degrees of alteration, from obvious to non-obvious. Therefore even a true pirate copy that they come upon will have a shadow of doubt cast on it beforehand: What if it's not real, but altered in some critical way that isn't obvious to tell without watching/listening/reading/etc. the whole thing?
The difference between this and prior attempts of producing decoys that are obviously false (i.e., very quickly detectable) is that here the complete spectrum is covered: There is significant doubt raised about the quality not just of the pirate file at hand, but all files one could download from pirate sources: the alterations would sometimes be obvious quickly, sometimes less so, sometimes not for a long time, and sometimes not clear until even after the pirate has e.g. watched the movie (and realizes later it lacked a crucial element, thus really feels annoyed at having invested so much time in the fake one that they're not likely to try a pirate copy again).
The whole concept is to introduce huge mistrust into the quality of pirate goods. When it isn't worth the effort to get a free copy of something that isn't the real thing, piracy is effectively dead. Consumers will have to purchase legitimate copies from trusted (legitimate) sources to be sure they have a correct copy and are not wasting their time. The diversity of quality levels ensures that if would-be pirates obtain many copies, they still will not know which, if any, are correct.
Pirates should, in fact, be encouraged to obtain as many of these false copies as possible, to "collect the whole set," since this assumes that they will also need to purchase a legitimate original. Piracy thus becomes a promotional tool.
Related Work A current strategy is the production of copies that are easily discernible from the originals, such as files of the same size but containing static, or endless repeats of brief portions of the original, or "educational" messages (e.g., the Madonna "What the fuck do you think you're doing" MP3 file).
The concept behind Shades of Gray is to produce a large number of different derivatives, many of which are substantially the same as the original, but different in varying degrees. This creates not merely minor irritation, but complete confusion over the veracity of all pirate downloads.
Ways of altering originals to produce "gray" copies If the original, unmodified data are considered "white," one could measure the "darkness" of the gray by comparing differences in the files from the original. For example, a gray copy that differs by one single bit from the original would be almost purely "white." A file that bears no discernible similarity to the original would be "black." A file that is 99% similar would be very light gray; a file 85% the same as the original would be light gray, and so on.
The modifications would be performed in ways to render the perception of a given gray copy to be as similar to the original as desired:
For example for books,
- character names interchanged (at random or consistently)
- selective frequent word changes that change the meaning (should -> would, may -> must, kill -> kiss, etc. etc.)
- chapters interchanged
- scenes from different chapters switched
- random sentences/paragraphs/scenes/chapters deleted
- middles of sentences missing so they don't make sense
- sentences from one part grafted into other areas (see www.ncww.org/bonsai.html for one implementation)
- chapters from other (e.g. public domain) works swapped in
- swap entire works (so would-be pirates find even the labeling can't be trusted)
- and so on.
- for films or other visual media, colors may be altered (subtly and/or noticeably; at some points in the film to whole film), brightness/contrast altered, images stretched, irritating visual noise introduced (random, or readable messages, etc.), scenes missing, extra scenes added, interchanged, every Nth frame deleted, mismatched with audio track, etc.
- for music or other audio data, going "warbly," soft, loud, shifting frequencies, cutting parts, screeches added, educational sound bites inserted, ...
- software programs may be modified so some copies do not save data (randomly or consistently), do not print correctly, do not properly perform desired functions, crash randomly or consistently, etc.
- software could likewise be modified to either clearly indicate to the user at some point that it is pirated (e.g. a pop-up); or could be modified to alert only the tech-support team (e.g. a serial number the user reports if they call tech-support that the support personnel identify as fitting a pattern of "gray" serial numbers) -- at which point the user could be urged to purchase the software and routed to a point of sale.
And other such similar changes that identify high quality products from lesser quality ones.
As a categorical kind of alteration, purely promotional material, such as movie trailers are to films, could also be used as gray versions of their original (since, indeed, each gray version can act as a promotional piece for the original).
All of these are easily done with software. Authors/artists might do their own, if they wanted to have fun.
Possible guidelines for deployment might be that in many copies the beginning (for example) 10% should be left untouched, to serve as a promotional advertisement for the work. After that, a sufficient amount of alteration should be introduced to make it clear to someone reading/watching/listing/using the item, after a while, that it's being a waste of their time to continue since it's not the original and differs in unknown ways; but not so much that it's instantly recognizable (to a person or to software). Gray copies should also be produced that are nearly identical to the original, but differ in some way, so that upon extensive, close inspection the differences could be detected. Yet other kinds of copies should be produced that are quickly recognizable as imperfect. The more diverse the spectrum of confusion the better.
Defeating work-arounds Pirates are likely to attempt to create work-arounds, such as publishing lists of how to identify quality copies (e.g., digital signatures). However, since (as pirates know) defeating a scheme is much easier creating a widespread and useful scheme, most schemes they would create are susceptible to defeat with more garbage (such as false lists of digital signatures). (This thus has the interesting property of using pirate techniques against them.) The goal is not zero tolerance, but merely to create sufficient distrust among the general population that they don't bother.
If lists are published of "known good" signatures, then gray-shaded lists may also be produced using the same techniques (completely false counter-lists that claim to come from the same "trusted" pirate source, lists that are partially correct and partially not, etc.). Alternate "gray" authorities may likewise be created, false personae who publish lists that are various shades of gray in correctness at different times. Additional alternate personae may be created to publicly praise another alternate persona's lists of signatures (or however it is that the pirates attempt to demonstrate the legitimacy of their versions).
The harder pirates attempt to prove the legitimacy of their versions the easier they become for law enforcement to track. (For example, if they register their public keys with reputable key repositories they are susceptible to being traced. The more reputable pirates try to become to clarify the quality of their product, the easier they will be to catch.)
This is, in fact, the lesson the pirates have been preaching themselves-- that it's typically easier to break a security scheme than implement it.
If pirates go deep underground, this is fine. If they only trust each other with the proverbial secret handshakes and it's difficult for most consumers to find -- or trust -- quality goods from pirate sources, then most people won't bother, and the financial impact from this piracy will be negligible. When the financial impact is minimized, the harm from piracy is essentially solved. The distrust issue is especially important: Even if someone trusts the source, will pirate "consumers" trust that what they received is really perfect? There should always be doubt: What if it were missing a bit... or a lot? The more shades of gray created, the less trust in pirate versions and the less acquisition of them.
The goal is therefore to make obtaining and trusting pirate goods so much work that it simply won't be worth it to the average person. There will always be a small minority who will be unstoppable, but if they have no financial impact, they don't matter. (In fact, if they desire to collect many different versions, that should be encouraged. It is, indeed, promotional material for the real product.)
Impact To whatever extent piracy is a financial difficulty, this invention renders it financially harmless. It does so without impacting legitimate consumers (i.e., there is no irritating copy protection scheme that intrudes on legitimate uses). Only those who seek pirated works are impacted. They are not harmed, except in choosing to waste their time to determine if a version is legitimate. This solution also eliminates the perception that piracy is a problem, not just the actuality, thus making producers of electronic products feel more comfortable releasing products without consumer-unfriendly copy protection schemes, etc.
This approach solves the piracy problem elegantly, and with as close to zero downside as can be imagined.
 |


 Dear America: Letters Home from Vietnam
Dear America: Letters Home from Vietnam The Box: The History of Television
The Box: The History of Television